



The Problems and Solutions of Bank Security Systems
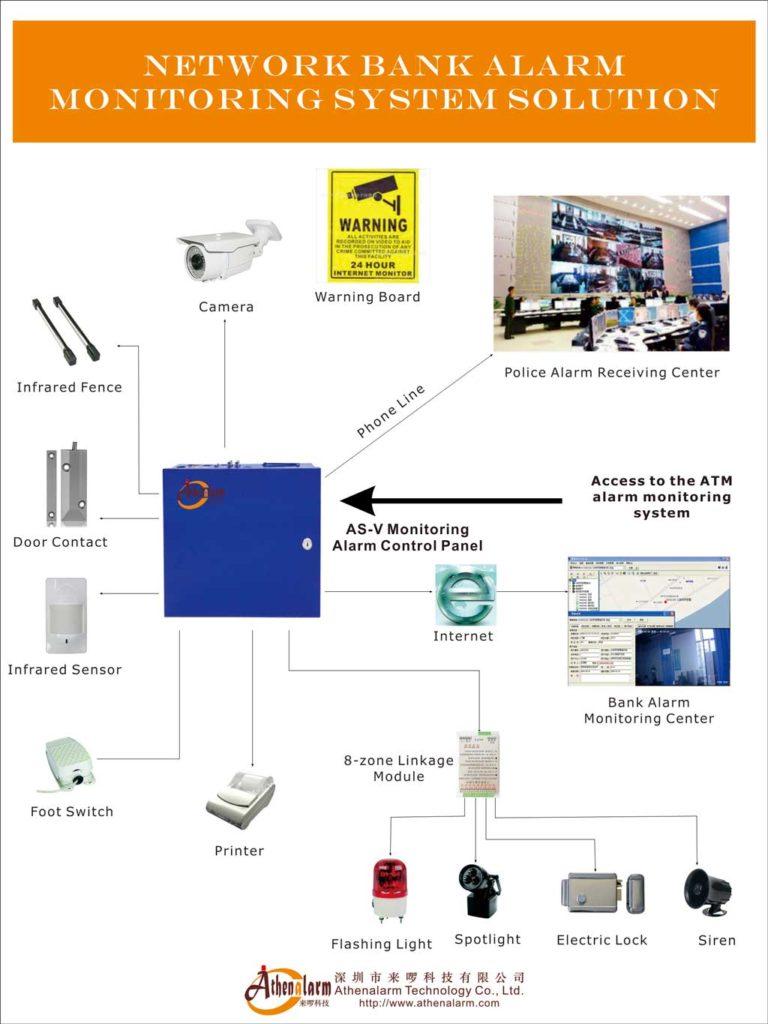
Banks are prime targets for criminal activities due to the high value of assets they hold, including cash, sensitive customer data, and digital transactions. To combat risks such as theft, fraud, and cyberattacks, robust security measures are essential. However, traditional bank security systems often suffer from fragmentation, outdated technology, and inefficiencies, necessitating a comprehensive overhaul to address modern security challenges.
This article provides a detailed analysis of the key security issues faced by banks and explores innovative solutions, integrating real-world applications and step-by-step operational enhancements.
1. Detailed Problems in Bank Security Systems
(1) Lack of Unified Supervision and Connectivity
- Many bank monitoring systems operate independently at different levels, from head offices to branches and ATMs. This disconnection prevents centralized management, making it challenging to achieve real-time supervision across the network.
- The lack of integration means security teams cannot efficiently coordinate responses, leading to potential delays in addressing threats.
(2) Limitations of Traditional DVR-Based Monitoring
Some banks rely on basic Digital Video Recorder (DVR) networking, which has several shortcomings:
- Centralized Management: Lacks unified authorization, making it hard to manage access across locations.
- Real-Time Monitoring: Struggles with simultaneous, low-latency viewing from multiple points, impacting response times.
- Video Quality and Retrieval: Often uses low-resolution formats like CIF, resulting in unclear footage, and retrieval is cumbersome, relying on manual searches.
- Manual Labor Dependency: High reliance on security personnel for alarm monitoring, increasing operational costs and error rates.
These issues highlight the need for a technological upgrade to enhance efficiency.
(3) Independent Security Subsystems Causing False Alarms
Security subsystems, including surveillance, intrusion alarm, access control, and fire alarms, typically operate in isolation. This lack of integration leads to:
- Frequent false alarms, which can desensitize security teams and waste resources.
- Missed alarms, as there’s no automated correlation with video footage for verification, increasing vulnerability to real threats.
The absence of linkage between systems exacerbates inefficiencies, requiring manual cross-checking.
(4) Low-Quality Surveillance Footage
- Many surveillance cameras still record in outdated CIF format, which fails to meet bank monitoring needs. The footage lacks clarity, color realism, and sufficient detail for identifying suspects or verifying incidents.
- This limitation is particularly problematic for high-stakes areas like ATMs and vaults, where clear identification is critical.
(5) Delays in Alarm Verification and Response
Traditional alarm monitoring centers depend heavily on manual verification processes, which are time-consuming. Security personnel must physically check each alarm, leading to:
- Delayed response times, potentially allowing criminals to escape or escalate threats.
- Increased operational burden, as manual processes are prone to human error and fatigue.
2. Comprehensive Solutions for Enhancing Bank Security Systems
To address these challenges, banks must adopt an integrated, technology-driven approach. Below are detailed solutions, including operational steps where applicable, to ensure a robust security framework.
(1) Implementing a Centralized, High-Definition Surveillance System
- Technology Upgrade: Deploy high-definition (HD) cameras, such as megapixel, 720P/1080P, and 4K models, equipped with advanced features like ultra-wide dynamic range, high-sensitivity Exmor CMOS, and infrared night vision. These enhance visibility in varying lighting conditions, crucial for 24/7 operations.
- End-to-End HD Architecture: Ensure the entire system, including storage, network transmission, and display, supports HD video. This requires upgrading backend infrastructure to handle higher data loads.
- Compatibility and Migration: Maintain backward compatibility with standard-definition devices to allow gradual migration. For example, existing cameras can be integrated while new HD cameras are phased in, reducing costs.
- Unified Management Platform: Implement a centralized platform with:
• Unified Authorization: Set up role-based access control, ensuring only authorized personnel can view or manage specific feeds. For instance, branch managers access local feeds, while head office oversees all.
• Real-Time Monitoring: Enable simultaneous, low-latency viewing from multiple points using high-bandwidth networks. Configure the platform to rotate feeds based on priority areas.
• Electronic Maps: Integrate multi-level electronic maps for quick camera selection and alarm location identification. For example, clicking on a map pin can display live footage from that location.
• Voice Intercom: Install intercom systems for real-time communication between central monitoring and branches, enhancing coordination during incidents.
• Equipment Patrol: Automate monitoring of device status, such as checking for video loss, network disconnection, or power issues. Set alerts for anomalies, ensuring proactive maintenance.
• Video Retrieval: Provide flexible retrieval options based on time, location, or event. For example, search for footage from 2 AM at a specific ATM by selecting the location on the map and setting the time range.
Operational Steps:
- Assess current camera inventory and network capacity.
- Select a management platform compatible with existing devices, such as those supporting DVR/DVS/NVR/IPC.
- Install HD cameras in high-risk areas like vaults and ATMs, ensuring coverage of all entry/exit points.
- Configure the platform for unified access, setting permissions for each user role.
- Test real-time monitoring and retrieval functions to ensure performance.
(2) Deploying an Integrated Alarm System with Video Verification
- Integration with Surveillance: Link intrusion alarm systems with video surveillance for real-time verification. When an alarm triggers, the nearest camera feed automatically displays on the monitoring screen.
- AI-Based Analytics: Use AI to differentiate between real threats and false alarms, such as distinguishing between a person and a passing animal. Configure the system to detect unauthorized access, loitering, or suspicious behavior.
- Access Control Enhancement: Integrate access control systems, using biometrics like fingerprint or facial recognition for enhanced authentication. For example, when a card swipe fails, the system can trigger an alarm and capture the individual’s image.
- Video Verification Process: Upon alarm activation, the system should:
• Display live footage from the nearest camera.
• Allow security personnel to verify the threat before dispatching a response team, reducing false alarms.
Operational Steps:
- Install motion detectors and access control devices at all entry points.
- Configure AI analytics to filter out common false alarms, such as wind-blown doors.
- Test the integration by simulating an unauthorized entry, ensuring the camera feed pops up and alerts are sent.
(3) Establishing an Alarm Monitoring System with Real-Time Automation
- Smart Alarm Processing: Automate alarm categorization based on severity and type, such as prioritizing forced entry over minor sensor triggers. Use AI to analyze patterns and reduce noise from non-critical alerts.
- Automated Notifications: Set up real-time alerts via mobile apps or smart devices for security teams. For example, an SMS or push notification can be sent to the nearest response team.
- Automated Security Protocols: Configure the system to trigger actions like locking doors, activating smoke or dye packs at ATMs, or notifying law enforcement during verified threats.
Operational Steps:
- Define alarm categories (e.g., high, medium, low) and set response protocols for each.
- Integrate with mobile notification systems, ensuring all team members have access.
- Test automation by triggering a mock alarm and verifying the response, such as door locks activating within seconds.
(4) Enhancing Cash Transport Security with GPS and GIS Integration
- GPS Tracking: Install GPS devices in cash transport vehicles to monitor real-time location. Integrate with the security platform for centralized tracking.
- GIS Mapping: Use Geographic Information System (GIS) to visualize routes on electronic maps, highlighting deviations or delays. Set geofencing to alert on unauthorized stops or route changes.
- Automatic Alerts: Configure the system to send instant alerts to security teams if a vehicle deviates from the predefined route, enabling rapid intervention.
Operational Steps:
- Equip all cash transport vehicles with GPS devices and connect to the central platform.
- Define standard routes and geofences using GIS software, such as setting a 500-meter radius around each stop.
- Test the system by simulating a route deviation, ensuring alerts are received and logged.
(5) Multi-Level Networking Architecture for Scalable Security Management
- Hierarchical Structure: Design a network connecting head offices, regional branches, and local outlets under a unified platform. Ensure each level can operate independently to prevent cascading failures.
- Permission-Based Access: Implement role-based access control, restricting data visibility based on user hierarchy. For example, branch staff see local feeds, while head office oversees all.
- High Reliability: Ensure system continuity with dual host standby, multi-machine clusters, and fail-over mechanisms. If one server fails, others take over seamlessly.
- Network Adaptability: Design for varying bandwidths, using local storage on DVRs for low-bandwidth areas and transmitting key images during alarms to higher levels.
Operational Steps:
- Map the bank’s organizational structure to design the network hierarchy.
- Configure access levels, ensuring compliance with data privacy laws.
- Test reliability by simulating server failure, verifying failover functionality.
(6) Integrating AI-Based Intelligent Analysis for Proactive Security
- Real-Time Threat Detection: Use Intelligent Video Surveillance (IVS) to monitor unmanned ATMs for suspicious activities, such as card skimming device installations. Configure AI to detect loitering or unauthorized access.
- Post-Incident Investigation: Implement AI-powered video analytics for quick retrieval of relevant footage. For example, search for all vehicles passing a specific location during a time range, filtering out irrelevant segments.
Operational Steps:
- Install AI-enabled cameras at ATMs and high-risk areas, configuring detection rules for suspicious behavior.
- Set up intelligent search parameters, such as filtering by vehicle color or person height.
- Test by simulating an incident, verifying the system retrieves relevant footage within minutes.
(7) Enhancing Cybersecurity in Security Systems
- Encryption and Access Control: Encrypt all security data and implement multi-factor authentication for access. Ensure only authorized personnel can view or modify settings.
- Network Segmentation: Isolate security systems on separate networks to prevent cyber intrusions affecting financial transactions. Use firewalls to block unauthorized access.
- Regular Testing and Updates: Conduct penetration testing quarterly to identify vulnerabilities. Apply firmware updates promptly to patch security holes.
- Compliance: Ensure adherence to standards like ISO 27001 for information security and PCI DSS for cardholder data, as well as local data protection laws.
Operational Steps:
- Audit current network security, identifying potential entry points for hackers.
- Implement encryption using tools like AES-256, and set up MFA for all access points.
- Schedule quarterly penetration tests with certified security firms, documenting findings and actions.
(8) Future-Proofing Bank Security Systems
- Cloud-Based Management: Adopt cloud storage for scalable video recording and retrieval, enabling remote access for security teams. Ensure encryption for data in transit and at rest.
- Blockchain for Secure Logs: Use blockchain to create tamper-proof access logs, enhancing audit trails for security incidents. This ensures integrity during legal proceedings.
Operational Steps:
- Migrate video archives to a secure cloud platform, such as AWS or Azure, with redundancy for disaster recovery.
- Implement blockchain logging for all access events, ensuring immutability and traceability.
3. Case Studies and Real-World Applications
To illustrate the effectiveness of these solutions, consider the following examples:
- Video Verification in Action: A leading international bank implemented video verification, reducing false alarms by 70%. When an alarm triggered, security personnel could instantly view live footage, confirming threats before dispatching teams, saving resources and improving efficiency.
- Automated Alarm Response in a Regional Bank: A regional bank integrated AI-powered alarm monitoring, cutting response time from 15 minutes to under 3 minutes. During an after-hours unauthorized entry, the system locked doors and alerted law enforcement, preventing a potential breach.
- Preventing a Cash Transport Heist: A European bank used GPS-based tracking for cash transport vehicles. When a truck deviated from its route, the system triggered an alert, allowing security to intervene before a robbery, demonstrating the value of real-time monitoring.
4. Summary and Recommendations
The evolution of bank security systems requires a shift from fragmented, traditional setups to an integrated, AI-driven, and networked infrastructure. Key improvements include:
- Transitioning to high-definition surveillance with video verification to reduce false alarms.
- Implementing AI-based alarm monitoring for real-time automation and quicker responses.
- Enhancing cash transport security with GPS and GIS integration.
- Establishing a multi-level network architecture for centralized management.
- Strengthening cybersecurity to protect against digital threats.
- Future-proofing with cloud-based and blockchain technologies for scalability and security.
By adopting these solutions, banks can create a robust, efficient, and future-ready security system, ensuring the safety of customers, employees, and assets in an evolving threat landscape.
