



Network Perimeter Alarm System Solution
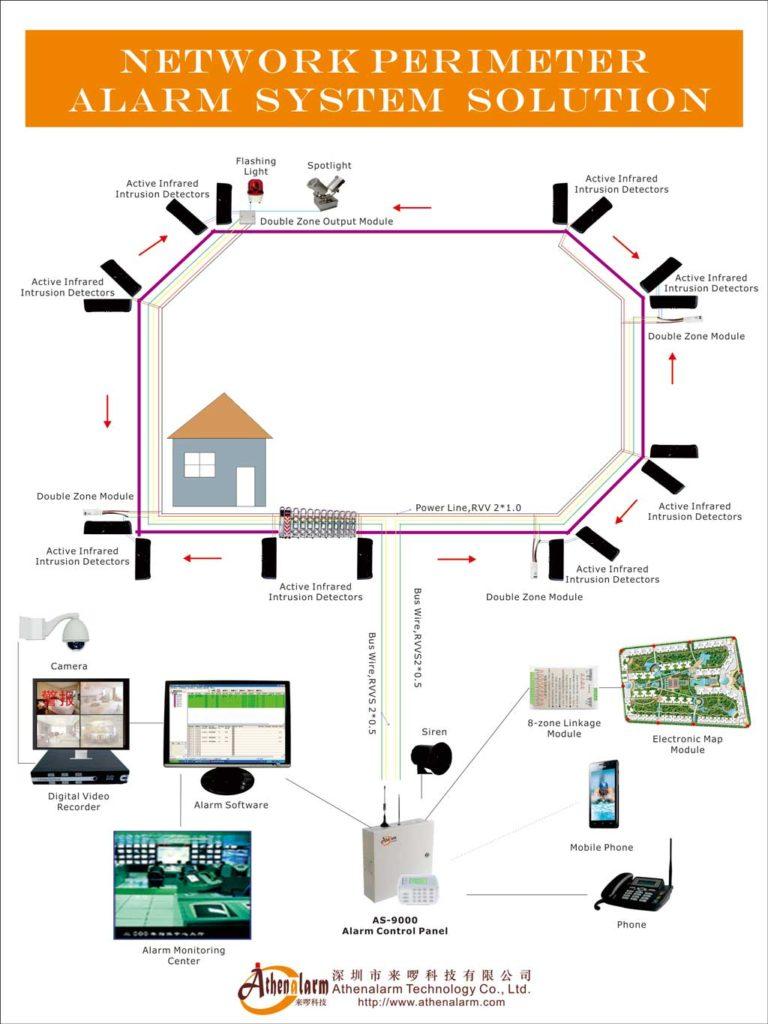
Table of Contents
ToggleOverview
With the advancement of society and heightened awareness of security, modern security technologies are now widely deployed. In critical areas such as parks, chemical plants, airports, military bases, weapons and ammunition depots, prisons, bank vaults, museums, power plants, and oil storage facilities, traditional methods of security often involve erecting barriers or obstructions—such as iron fences, wire mesh fences, and similar structures—around the perimeter, accompanied by regular patrols. However, as criminals increasingly employ sophisticated technologies and more complex, intelligent tactics, these conventional methods are no longer sufficient to meet the security needs of key sectors and institutions. Human-based defense systems are often vulnerable to limitations such as time constraints, location challenges, personnel quality, and energy factors, leading to inevitable gaps and errors. Consequently, the installation and implementation of an advanced perimeter alarm system has become a crucial necessity.
Introduction to Perimeter Alarm Systems
What is a Perimeter Alarm System?
A perimeter alarm system is designed to secure the outer boundaries of a property or facility, acting as the first line of defense against unauthorized access. These systems detect and alert security personnel to any breaches in the perimeter, such as fences, walls, or open spaces surrounding the premises. Perimeter alarms are crucial for protecting valuable assets, ensuring safety, and preventing intrusions.
Why is Perimeter Security Important?
As crime rates rise and criminal tactics evolve, relying solely on indoor security measures such as surveillance cameras and alarms is no longer enough. A perimeter alarm system helps detect potential threats before they enter the property, reducing the risk of damage or loss.
Types of Perimeter Alarm Systems
Infrared Beam Systems
Infrared perimeter detection works by sending a beam of light across the perimeter, which is interrupted when an intruder crosses it.
- Best Use Case:
• Fences with clear sightlines
• Open fields or properties with little vegetation
• Suitable for indoor and outdoor environments - Limitations:
• Prone to false alarms due to environmental factors such as heavy rain, fog, or snow
• Requires careful installation to avoid obstructions that could block the beam
• Limited range, may not be suitable for larger properties
Video Surveillance Integration
While already mentioned, the advantages of integrating video surveillance with perimeter alarms could be expanded. By combining real-time video feed with motion detection, security teams can have immediate visual confirmation of any potential intrusions.
- Best Use Case:
• Large facilities and high-value areas where visual confirmation of an intrusion is necessary
• Locations requiring real-time surveillance to monitor activity - Limitations:
• Requires significant storage and data processing capacity
• May be less effective in poor lighting or adverse weather conditions
Electric Security Fences
In addition to the existing content, elaborating on the technology behind electric security fences would add value.
- Best Use Case:
• High-security environments such as prisons, military bases, and government facilities
• Areas where physical barriers need to be reinforced with an active deterrent - Limitations:
• Visible fencing may be unsightly for residential areas
• May require regular maintenance to ensure the electrical system remains functional
• Can be costly to install compared to other perimeter security options
Ground-based Detection Systems
Ground sensors, such as buried cables, seismic sensors, and pressure mats, could be discussed as another layer of perimeter security. These systems detect ground vibrations or pressure changes when someone steps on or moves near the sensors.
- Best Use Case:
• Areas where visibility of other security measures may be impractical or undesirable
• Locations with complex terrain where visual surveillance is difficult - Limitations:
• Prone to false alerts from animals or natural environmental changes
• Installation can be complex and costly, especially in large areas
Choice of Perimeter Alarm System
Currently, the three most commonly used perimeter alarm systems are video surveillance, infrared beams, and electric security fences.
Video Surveillance
Intelligent video motion detection and tracking systems are employed in perimeter alarms, leveraging digital video image analysis and processing technology to analyze and process surveillance footage of the perimeter area. The system can detect human activity, identifying whether the movement is normal, if someone is attempting to cross the perimeter, or if objects are being thrown or abandoned near the boundary.
Once an intrusion is detected, the system triggers an alarm and initiates various linked actions. The video feed provides a direct view of the alarm event, making the traditionally invisible perimeter area now visible.
While video surveillance offers clear advantages, such as visualization, automatic tracking, and the ability to record and replay footage, it also has notable drawbacks. For instance, the system’s effectiveness is reduced in hazy weather or at night, and there are blind spots in coverage. Additionally, it cannot actively warn intruders, and the system may degrade over time.
Infrared Beam
Infrared beams have no physical barrier and are primarily used for alarm purposes. Their main advantages are low cost and ease of installation. However, they are subject to limitations imposed by environmental factors, such as terrain variations, twists, turns, and weather conditions. Their protection capability is low, and they are not well-suited for harsh climates. Extreme temperatures, strong sunlight, dust, rain, snow, fog, and frost can all cause malfunctions, resulting in a high false alarm rate.
The positive infrared beam is one of the most commonly used perimeter alarm systems for residential communities. When an intrusion occurs, the system triggers an alarm, but the intrusion may already have taken place, putting personal and property safety at risk. To mitigate this, many communities combine the infrared system with additional barriers or obstructions (such as iron fences, glass walls, or wire mesh) and rely on patrolling personnel.
Due to the inherent limitations of the infrared beam technology, false alarms are common in outdoor environments, particularly in adverse weather conditions like rain, fog, or strong winds.
Electric Security Fence
The electric security fence serves three primary functions: deterrence, blocking, and alarm. It offers active prevention, robust environmental adaptability, and is unaffected by temperature changes or environmental factors such as vegetation, small animals, or terrain variations.
This system provides precise positioning and a strong deterrent effect. If an alarm is triggered and a criminal persists in attempting to breach the perimeter, the system responds with a powerful electric shock, further discouraging unauthorized entry.
Electric security fences are particularly suitable for securing critical locations such as factories, airports, warehouses, high-end villas, luxury residences, and other large-scale defense areas.
Recommendation: To achieve optimal perimeter security, it is advisable to combine these three systems for a multi-layered defense approach.
Composition of the Perimeter Alarm System
A perimeter alarm system typically consists of four key components: front-end detectors, a signal transmission network, a central alarm control panel with alarm center management software, and audio-visual alarm devices.
To enhance the effectiveness of the security system, the perimeter alarm system is often integrated with a monitoring system, enabling real-time situational awareness of the alarm events. The monitoring system provides 24/7 surveillance of the perimeter area and supports computerized management, allowing security personnel to promptly and accurately assess the surrounding environment. In the event of unauthorized access, the system will automatically trigger an alarm, identify the alarmed area, and record the incident. It will also forward the alarm data to relevant parties. Additionally, when equipped with video surveillance, the system can provide real-time visual and recorded footage of the deployment and control site, offering reliable information for alarm validation and post-event response.
While the technology used in the front-end detectors may vary, the other components of the perimeter alarm system generally follow similar configurations.
Integration with Other Security Systems
Access Control Systems
Integrating perimeter alarms with access control systems (e.g., key cards, biometric scanners) ensures that not only intrusions are detected, but access to the premises is also restricted to authorized personnel only.
Intruder Alarm Systems and Panic Buttons
When a perimeter alarm is triggered, integrating with an intruder alarm system ensures that the premises are locked down, and the alarm is escalated to appropriate authorities. Panic buttons could also be connected to perimeter alarms, allowing security personnel to escalate the situation quickly.
Mobile and Cloud-Based Monitoring
Many modern perimeter alarm systems can be integrated with mobile apps or cloud-based security platforms. This allows security personnel or property owners to monitor perimeter events in real-time from anywhere, increasing the flexibility and responsiveness of the security system.
Best Practices for Perimeter Alarm Installation
- System Placement and Coverage: The effectiveness of a perimeter alarm depends heavily on the correct placement of sensors and detectors.
- Regular Maintenance and Testing: Perimeter alarm systems require regular maintenance to remain effective.
- Environmental Considerations: The environmental factors such as extreme temperatures, humidity, or even vegetation can affect perimeter alarm systems.
Legal and Compliance Considerations
- Local Regulations: Depending on the region or country, there may be legal restrictions or regulations regarding the use of certain types of perimeter alarm systems (e.g., electric fences, surveillance cameras).
- Privacy Considerations: When using video surveillance as part of a perimeter alarm system, we need to ensure the system respects privacy laws. We should be aware of where cameras are positioned to avoid monitoring public spaces or neighboring properties, and data storage should be handled securely.
Common Challenges and Solutions
- False Alarms: Provide strategies for reducing false alarms, such as using dual technology sensors, incorporating environmental sensors, and setting up alerts based on multiple factors. For instance, combining motion detection with video verification can help minimize unnecessary alerts.
- Power Failures: Offer solutions for ensuring system continuity during power outages, such as backup power sources, solar panels for outdoor systems, or UPS (Uninterruptible Power Supply) systems for critical equipment.
Conclusion
In this article, we’ve explored the key aspects of perimeter alarm systems, including their importance in safeguarding valuable properties and sensitive areas. We’ve covered the most common types of perimeter security solutions—such as video surveillance, infrared beams, and electric security fences—highlighting their advantages, limitations, and ideal use cases. Additionally, we’ve discussed how integrating these systems with other security measures can provide comprehensive, multi-layered protection.
Whether you’re securing a residential area, commercial facility, or high-security site, choosing the right perimeter alarm system is crucial for effective protection. By understanding the different options and how they can be tailored to your specific needs, you can ensure peace of mind and enhanced security.
Take the Next Step in Securing Your Property
If you’re ready to enhance your perimeter security, don’t hesitate to contact us today! Our experts are here to help you find the perfect solution tailored to your needs. Leave your contact details, and let’s work together to ensure your property remains safe and secure.
