



Network Alarm Monitoring System Solution
Table of Contents
ToggleOverview
Currently, many network alarm systems rely on traditional communication methods such as landline phones and GSM technology. However, with the advancement of modern science and technology, new security systems supported by cutting-edge technological products are playing an increasingly vital role in the broader social security framework.
Among these, cloud-based network alarm and monitoring systems offer essential functions, such as real-time alerts and the ability to receive and handle alarms. These systems are well-suited to the needs of large-scale public security management. By using these systems, an alarm monitoring center can be established, enabling the rapid deployment of security forces. As such, the network alarm system and monitoring system represent the most critical subsystems within the social security infrastructure.
The key challenge today is to effectively harness the full potential of the network alarm system, seamlessly integrate it with monitoring systems, and develop a unified, stable, and highly expandable alarm monitoring system that adapts to social developments. This has become one of the most pressing demands in the current security industry.
Disadvantages of Traditional Network Alarm Systems
Traditional network alarm systems primarily rely on landline phones and GSM technology for communication. These systems consist of three main components: the user terminal, the communication medium, and the alarm center. The user terminal typically includes the alarm control panel and various detection sensors; the communication medium is generally the public switched telephone network (PSTN); and the alarm center is equipped with a dedicated digital alarm receiver, alarm management computers, and corresponding software.
The user terminal requires at least one alarm control panel, which processes sensor signals and is responsible for communication and alarm functions. Depending on the type of protection needed and the potential risks, different numbers and types of sensors are selected. Once the alarm control panel receives the signal from a sensor, it transmits the information to the alarm center via the public switched telephone network. Alarm control panels equipped with GSM functionality can also communicate the alarm signals to remote user members.
Traditional network alarm systems, while reliable, are increasingly constrained by factors such as geographic limitations and the number of users. Despite these challenges, they offer advantages such as rapid response times, high capacity, and flexible organization.
The following diagram illustrates the structure of a traditional network alarm system:
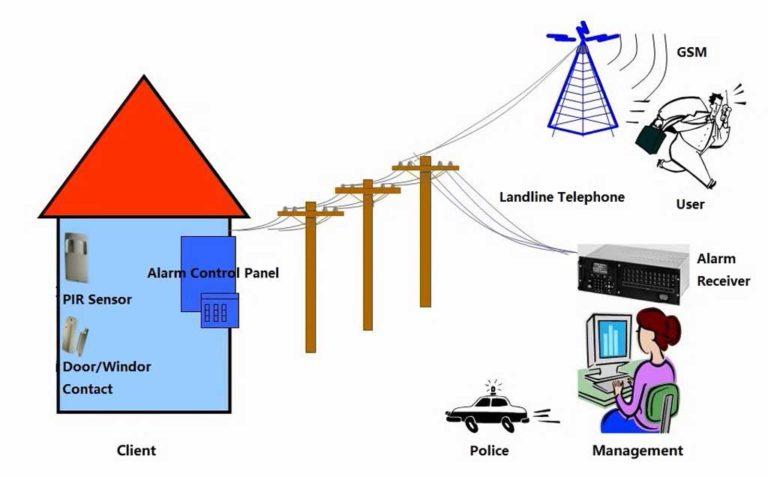
This type of communication network offers several advantages, including a widely accessible network environment, mature technology, and low hardware costs, ensuring its continued use for an extended period. However, it is important to recognize that this communication method also has inherent limitations:
- High communication costs and elevated system operational expenses;
- Due to channel limitations and cost constraints, achieving two-way real-time communication is challenging, and establishing remote control may take a significant amount of time with a low connection rate;
- The system is vulnerable to disruptions, and the alarm center may not be immediately aware if the communication is compromised, leading to a high risk of system failure;
- User applications in remote or rural areas, or in specific industries, are limited.
Currently, as alarm systems become more widely adopted and awareness of these systems grows, individuals with malicious intent have begun exploiting the vulnerabilities of wired communication to conduct targeted sabotage, resulting in losses for many users.
Furthermore, relying solely on the alarm system means that when an alarm occurs, users are only informed of the event and lack real-time insight into the alarm situation. This necessitates notifying security personnel to respond to the scene before any action can be taken. Additionally, users are unable to capture evidence at the time of the alarm, complicating post-event analysis. Relying solely on the alarm system presents significant shortcomings in terms of processing efficiency, cost, and overall effectiveness in handling alarm situations.
Disadvantages of the Network Alarm System and Monitoring System
With the continuous advancement of information technology, the emergence of GPRS wireless network communication modules and TCP/IP wired network communication modules based on IP technology has revolutionized communication methods, replacing the traditional landline telephone and GSM communication systems. Today, GPRS wireless communication has evolved to 4G and 5G networks, with ongoing development.
In the security sector, alarm control panels now integrate landline telephones, wireless network communication modules, and wired network communication modules, effectively fulfilling the core functions of low-cost network alarms, rapid communication, high efficiency, stability, and front-end user anti-tampering. Users with varying needs can select one or more of these communication modules to enhance the alarm communication capability of the panel and establish an IP-based network alarm system. The diverse communication methods employed by alarm control panels enhance system communication reliability and increase the system’s resistance to tampering. Compared to traditional alarm systems, the current network alarm system has made significant improvements in communication and transmission methods. Furthermore, IP-based monitoring systems are being widely adopted across various sectors of society.
Network alarm systems and monitoring systems have proven advantageous and have become widely deployed in security applications, including in security companies, banks, residential communities, government entities, businesses, key retailers, warehouses storing critical materials, and important private residences. However, these network alarm and monitoring systems currently operate independently of one another. When an alarm is triggered, the network alarm system sends the alarm information to the monitoring center, where personnel must separately search and review the monitoring system to assess the situation at the alarm site. Moreover, the video footage available is recorded after the alarm has been triggered, requiring further review to understand the events surrounding the alarm. This process is time-consuming, labor-intensive, and inefficient, failing to meet the needs of contemporary security management.
The key challenge in today’s security field is to effectively integrate the alarm system with the monitoring system, creating a unified, reliable, efficient, and user-friendly network alarm monitoring system.
Functions of the Athenalarm Network Alarm Monitoring System
The Athenalarm network alarm monitoring system effectively integrates the network alarm system with the monitoring system (CCTV) and includes features such as real-time video review. When an alarm is triggered, the system can automatically display live video from the alarm site. This system is designed to meet the following requirements:
- In the event of dangerous situations such as burglary, robbery, or fire, when the alarm control panel automatically or manually triggers an alarm, the alarm information is transmitted based on the user’s communication conditions. This information can be sent through various communication methods, including the telephone network, wireless network (mobile network), and wired network (broadband data network). The information is then uploaded to the central alarm monitoring center. The alarm monitoring center can forward the information to other alarm monitoring centers, both up and down the chain, while analyzing the alarm data. This allows law enforcement to be deployed effectively to handle the situation on-site, enabling automation of the command process.
- The network alarm monitoring system also ensures seamless integration between the alarm system and the monitoring system (CCTV). When an alarm is triggered, real-time video from the alarm site is automatically displayed, with the option to record and save the footage immediately.
- Additionally, the network alarm monitoring system features a comprehensive operation and maintenance management function, enabling constant monitoring of equipment status. Remote diagnostics and maintenance can be performed as needed.
- The system also supports business operation management capabilities, allowing for the querying, counting, and printing of network user information and generating various required statistical reports. These reports may include maintenance, inspection, payment, and other information lists, which can be accessed at any time.
(For more details, please refer to the Network Alarm Monitoring System Application.)
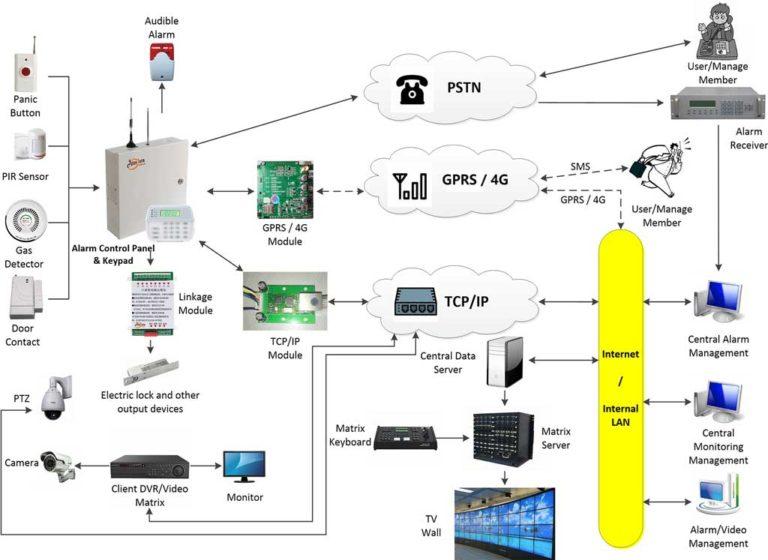
System Structure of the Network Alarm Monitoring System
The network alarm monitoring system is comprised of three main components:
1) Alarm Software: The AS-ALARM network alarm center management software is the central management system for the alarm monitoring center. It consists of two components: the server and the client. The server requires installation on Windows Server 2008 or Windows Server 2012 (users can choose to build or rent a server). The client software can be installed on any Windows OS personal computer with internet connectivity. (Refer to the AS-ALARM Network Alarm Center Management Software documentation for details.)
2) Alarm System: The alarm system includes the Athenalarm alarm control panel, detection devices, linkage equipment, and other related products.
3) Monitoring System: The monitoring system includes products that are compatible with the alarm software, such as surveillance equipment from brands like Hikvision, Dahua, and other similar providers.
The system structure for this solution is illustrated below:
Advantages of the Network Alarm Monitoring System
The network alarm monitoring system offers significant enhancements over traditional network alarm systems. It strengthens the communication capabilities of the user-end alarm control panel and incorporates a data linkage interface in the alarm software, thereby significantly improving communication reliability, scalability, and system integration.
- Enhanced Communication Modules: Communication capability is a critical component of any network alarm system. This system supports both wireless and wired network communication modules, enabling the front-end alarm control panel to enhance its alarm capabilities via LAN and WAN in addition to conventional telephone-based alarms. The system supports dual-network or even triple-network communication, greatly enhancing its adaptability to various communication environments and significantly improving overall safety and reliability.
- Advanced Alarm Software: The AS-ALARM network alarm center management software provides an open data channel that allows for seamless data exchange with other security subsystems on the alarm monitoring center’s LAN. This facilitates integrated linkage at the software level, enabling efficient collaboration between the alarm monitoring center and other security systems.
- Video Linkage Functionality: The system integrates with mainstream video servers, enabling the user-end alarm system and monitoring system to establish extensive, multi-point programmatic linkages. This feature enhances the functional capabilities of the system, offering a higher level of overall integration and operational efficiency.
These advancements make the network alarm monitoring system a superior solution for modern security challenges, offering improved performance, reliability, and integration across diverse security applications.
Features of the Network Alarm Monitoring System
The Athenalarm Network Alarm Monitoring System incorporates several key features designed to provide robust functionality, adaptability, and reliability:
1) Openness
The system includes numerous general-purpose hardware and software interfaces, making it both a standalone solution and easily integrable into existing or future emergency systems. For instance, it can forward alarm information to public security systems to unify social security and resource allocation or connect alarm signals from access control, fire protection, and other systems. These systems can share the same communication environment and platform for efficient information transmission and resource sharing.
2) Reliability
The AS-ALARM network alarm management software has been successfully implemented in tens of thousands of alarm monitoring centers across various levels and regions. Additionally, the Athenalarm professional burglar alarms deployed at user locations have been widely adopted in China and internationally, with tens of millions of units in use, particularly in industries such as finance and telecommunications. This extensive track record underscores the system’s exceptional reliability.
3) Advancement
The Athenalarm alarm control panel and its accessories are proprietary, self-developed products. These innovative components grant the system unparalleled adaptability to diverse communication environments, along with superior alarm and expansion capabilities. This technological edge significantly enhances system performance, cost-effectiveness, and reliability.
4) Extensibility
The system is highly scalable and can be easily upgraded or expanded to accommodate a growing number of network users. Scaling the system requires only the addition of corresponding communication lines and alarm hardware without disrupting normal operations. System capacity can range from hundreds to millions of users. On the user end, the alarm host’s bus function allows for expansion of defense zones and external linkage devices. Adding more alarm control panels is straightforward—simply connect the new panels to the communication network.
5) Operability and Maintainability
The system is designed not only to receive alarm information but also to monitor real-time status updates, such as equipment malfunctions, ensuring effective user protection. The alarm software allows for querying, statistical analysis, and reporting of user-related data, including alarm events, faults, and payment records. Leveraging Athenalarm’s extensive experience in service delivery and technical support, the system enables rapid establishment of citywide network alarm monitoring centers and provides ongoing operational and management support.
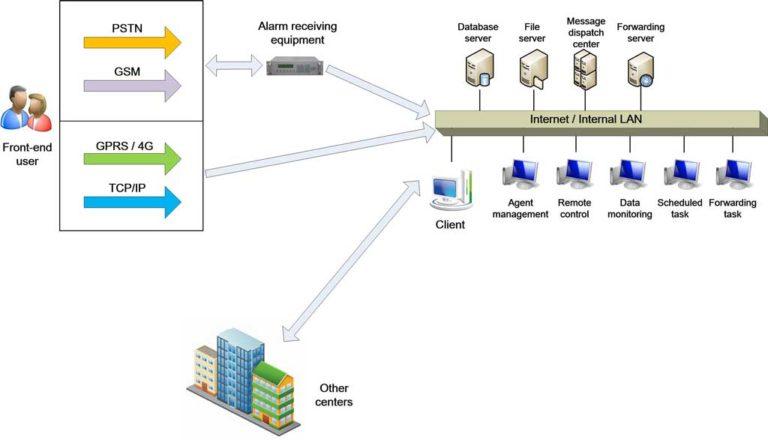
AS-ALARM Network Alarm Center Management Software
Structure Diagram of the Alarm Software
Features of the Alarm Software
- Large user capacity: The software uses a large-scale SQL Server database system, and the capacity of a single database table far exceeds 1 million, which is beneficial to the continuous increase of the number of users.
- Modular function design: The entire system adopts a modular design, and corresponding function modules can be added according to the functional requirements of different users. Users can easily add functions without destroying the system. According to different management methods, change the application mode of the system to greatly improve work efficiency.
- Powerful management function: The system management is handled by a special management computer, and the processing function is very powerful. According to processing and management methods, analyze related events and information to complete the work in a timely and effective manner.
- High system stability: The system data is carried by a dedicated database server and application server, which greatly increases the data capacity and data exchange capacity of the entire system, and greatly improves the stability of the system. This reduces the effort of system maintenance and can handle the center’s related work with peace of mind.
- Multi-level networking is more convenient: TCP/IP network can be used for remote network transmission. The separation of police handling and management and detailed work responsibilities are conducive to unified management.
- Complete system backup function: It can realize online backup of alarm records, user data, system logs, and other data and restore the backup data. It supports dual-system work and backup. Two servers share data at the same time. When one server stops working, the other server automatically connects to the system and continues to work to ensure the security of the system.
- Support multiple alarm receiver hardware: dedicated modem, alarm receiving card, professional alarm receiver from multiple mainstream manufacturers, especially good at network alarm receiving.
- Super compatibility: compatible with multiple communication formats alarm control panel: It can receive information reported by the alarm control panel produced by major equipment manufacturers on the market, and is compatible with multiple communication formats such as C&K CFSK III, ADEMCO Contact ID, ADEMCO 4+2 Express, etc.
- Support multiple video equipment: The software supports many well-known video equipment on the market, including Hikvision, Dahua, EZVIZ, Univision, etc.
- Strong security: The level of operators in this software has multiple levels such as system administrator and operator (custom level). Each operator can operate different data content, which can realize the separation of tasks.
Functions of the Alarm Software
- Map function: The map function is to use the Baidu map and bitmap to represent the user’s defense zone map. The alarm control panel and defense zone’s alarm hotspots can be marked on the Baidu map. The defense zone map can mark the user’s subsystems and defense zone’s alarm hotspots on the map to realize the corresponding defense zone hotspots after the alarm. It flashes to remind the user of the specific alarm location, which is convenient for the police to deal with in time.
- Video linkage function: The software can link the defense zone with the video. When an alarm occurs in the defense zone, the real-time video of the corresponding defense zone will automatically pop up, and it can be recorded and played back.
- User event query and statistics function: It has a powerful statistical report function, and uses the method of comprehensive condition query to find the required data report.
- User data management function: add new user, modify user, load user, user query, user sort, delete user, and list printing.
Export function: The alarm control panel event report, user list, and user information, alarm handling documents, etc. can be converted into text, WORD, EXCEL files for re-editing, which realizes the diversity of data, and is conducive to the archiving of data. It can also be set according to the user statistical printing of the restriction conditions. - Operator record management: It is mainly the management functions of adding, editing, and authority setting to operators.
- Database management: The database management function is the operation of data backup, restoration, and sorting.
Multiple alarm control panel type management: The diversity of alarm control panel types is enhanced. The alarm center for unified control of multiple alarm control panels can customize the type of the user’s front-end control alarm control panel, and the alarm control panel classification is more detailed and the query is more convenient. - Custom coding scheme: You can set a custom decoding scheme for the communication protocol 4+2 and the CONTACT ID communication protocol, and edit and delete the newly added scheme.
- Unique remote programming and grasping function: mainly for Honeywell 2300 series alarm control panel.
- Alarm forwarding function: In order to communicate with other alarm centers, the Alarm7.0 alarm receiving system is equipped with the function of forwarding report information via telephone and IP.
- Caller ID: It can be used to query telephone line problems. It is conducive to the detection of malicious or unintentional blocking of the communication of the alarm center, and the locking of users who have failed in communication, incomplete information, and changed data. However, corresponding access equipment (multifunctional alarm receiving card) is required to assist in completion.
- Extended upgrade function: convenient secondary development, Alarm7.0 alarm receiving system provides an open database system with DDE and Socket interfaces, which is conducive to the secondary development of users, and can also customize a specific version according to customer needs.
