



The Alarming Truth About Burglar Alarm Monitoring You Can’t Ignore
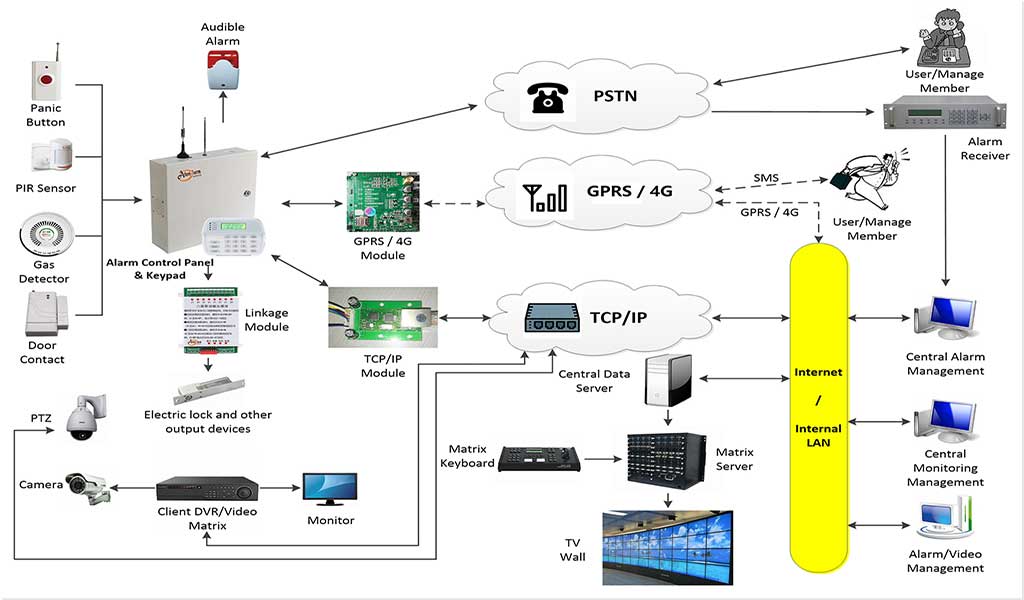
Table of Contents
As a security systems expert with decades of experience in both high-risk commercial environments and emerging smart infrastructure, I can confidently say this: Burglar alarm monitoring is not just a technology—it’s a business-critical decision. In this article, I’ll walk you through the 7 critical facts that every professional in the security industry must understand to implement effective, future-ready, and risk-proof alarm monitoring systems.
Burglar Alarm Monitoring is the professional process of continuously observing intrusion detection systems to ensure immediate response to security breaches. Unlike standalone alarms, monitored systems transmit real-time alerts to centralized control centers, where trained professionals verify, escalate, and respond to events. This 24/7 service reduces false alarms, increases emergency response efficiency, and aligns with insurance and regulatory compliance—making it indispensable in today’s risk-sensitive environments.
Burglar Alarm Monitoring Is a 24/7 Mission-Critical Operation
Today’s advanced burglar alarm monitoring systems are built for nonstop protection. Behind every sensor and alert is a central monitoring station, staffed 24/7 by trained operators ready to respond to emergencies in real time.
Why It Matters: A delay of even a few seconds can turn a minor incident into a major catastrophe. Real-time monitoring turns your system from a reactive siren into a proactive defense layer.
Implementation Tip: Choose UL-listed monitoring centers that meet industry certifications like TMA Five Diamond, and verify their average response time.
Every Component in the System Must Work Flawlessly
A burglar alarm system is only as effective as its weakest link. Hardware and software elements must operate in perfect sync for reliable detection and communication.
Key components include:
- Control Panel – The system’s brain, processing all inputs.
- Perimeter Sensors – Monitor door/window breaches or glass breaks.
- Interior Motion Detectors – Detect unauthorized movement indoors.
- Audible/Visual Alerts – Sirens and strobes that deter intruders.
- Communication Modules – Relay alerts via IP, cellular, or landline.
- Backup Power Supplies – Maintain operation during outages.
Expert Warning: Many legacy systems lack encryption or integration with mobile/cloud platforms. Annual health checks are non-negotiable.
Alarm Activation Workflow Directly Impacts Response Outcomes
Your system’s internal logic—how it detects, verifies, and signals—is the operational engine of alarm monitoring.
Recommended workflow:
- Event Detection: A sensor picks up unusual activity.
- Signal Verification Logic: Filters out false positives.
- Alarm Activation: Triggers sirens and sends the alert.
- Remote Notification: Alerts monitoring stations and users.
Avoid This Pitfall: Misconfigured entry/exit delays lead to false alarms and delayed response. Always calibrate sensitivity zones and timing intervals.
Signal Transmission Must Be Redundant and Encrypted
If your alarm signal doesn’t reach the monitoring center, everything else fails. That’s why redundant and secure communication paths are mission-critical.
Common transmission types:
- Cellular (GSM/LTE) – Resilient, tamper-resistant.
- Internet Protocol (IP) – Fast but dependent on broadband.
- Landline (POTS) – Obsolete, vulnerable to cuts.
Best Practice: Deploy dual-path or tri-path communication with AES-128 or higher encryption, and ensure automatic failover protocols are in place.
The Monitoring Center Is Your Emergency Command Center
The monitoring center is where the real value of burglar alarm monitoring is realized. It’s here that speed, training, and procedures directly influence your risk exposure.
Standard protocol:
- Signal received within 2–5 seconds.
- Operator contacts designated stakeholders.
- Emergency services dispatched immediately.
- Full event logging for audits and claims.
Benchmark: A total response window of under 30 seconds is the gold standard in high-security environments.
The Industry Is Rapidly Evolving—Your System Must Be, Too
Security tech is no longer static. From AI-driven analytics to geofencing, burglar alarm systems must integrate with broader digital ecosystems.
Emerging trends:
- AI-Powered Detection – Identifies behavior anomalies.
- Video Verification – Links alerts with CCTV feeds.
- Cloud-Based Management – Enables updates and diagnostics remotely.
- Geofencing – Automates arming/disarming via GPS.
- Open APIs – Allow integration with VMS, access control, and ERP systems.
Strategic Insight: Choose vendors offering modular, scalable platforms to keep your system agile and interoperable.
Professional Monitoring Beats Self-Monitoring in High-Risk Use Cases
Consumer-grade apps cannot match the depth and reliability of professional monitoring—especially in critical infrastructure, retail chains, or data centers.
| Feature | Self-Monitoring | Professional Monitoring |
| Availability | User-dependent | 24/7 staffed center |
| Verification | Manual | Operator-assisted |
| Emergency Dispatch | Delayed | Immediate |
| Compliance | Often non-compliant | Fully certified |
Bottom Line: For B2B operations, professional monitoring isn’t optional—it’s essential. Skipping it invites regulatory penalties, reputational damage, and financial loss.
Conclusion
If you’re a security decision-maker, you can’t afford to overlook these 7 facts. Burglar alarm monitoring is not a checkbox—it’s a strategic asset. By investing in robust infrastructure, intelligent workflows, and professional response capabilities, you future-proof your operations and safeguard your assets with confidence.
Final Thought: The investment in professional alarm monitoring is minor compared to the devastating cost of a single unmitigated breach. Prioritize smart. Act now.
FAQs
Q1: What is burglar alarm monitoring and how does it work?
A1: Burglar alarm monitoring involves real-time oversight of intrusion systems by professional centers that verify and respond to alerts, ensuring immediate action.
Q2: Why is 24/7 monitoring important for businesses?
A2: It guarantees continuous protection, reduces response time, and ensures compliance with insurance and legal standards.
Q3: What components make a burglar alarm system effective?
A3: Key components include a control panel, sensors, communication modules, backup power, and audible/visual deterrents.
Q4: How does alarm signal transmission work?
A4: Signals are sent via cellular, IP, or landline paths, often using encrypted dual-path or tri-path setups to ensure failover reliability.
Q5: What’s the difference between self-monitoring and professional monitoring?
A5: Self-monitoring relies on user response, while professional centers ensure 24/7 availability, faster dispatch, and regulatory compliance.
Q6: Can AI be integrated with alarm systems?
A6: Yes, modern systems use AI for behavior-based detection and to reduce false alarms through learning algorithms.
Q7: What is the recommended response time for a monitoring center?
A7: Optimal total response time—including signal reception, verification, and dispatch—is under 30 seconds.
Q8: How do I ensure my alarm system is compliant with industry standards?
A8: Use UL or EN-certified systems, and ensure your monitoring center meets TMA Five Diamond or equivalent standards.
Q9: Are cloud-based alarm systems reliable?
A9: Yes, if paired with robust security protocols and dual communication paths, they offer superior flexibility and diagnostics.
Q10: How often should a burglar alarm system be audited?
A10: At least once a year, or after any major event, upgrade, or environmental change.
